Twice Bypassed and Twice Micropatched, Will Third Time be a Charm?
by Mitja Kolsek, the 0patch Team
Update 8/10/2022: April 2022 Windows Updates brought an official fix for this vulnerability with assigned CVE-2022-26904. Our users were therefore protected from this issue whole 22 days before an official fix got available, and remained protected until they installed Windows Updates. These micropatches from now on require a PRO or Enterprise license.
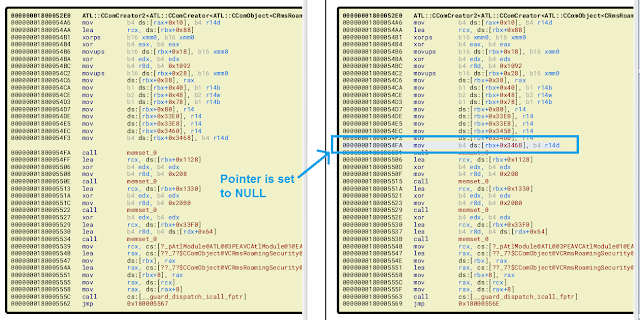
In November we issued a micropatch for a local privilege escalation in User Profile Service .This vulnerability was found and reported to Microsoft by security researcher Abdelhamid Naceri and assigned CVE-2021-34484 when initially fixed. Abdelhamid subsequently noticed that Microsoft's patch was incomplete and wrote a POC to bypass it. Based on that information, we were able to create a micropatch for what was then considered a 0day (a known vulnerability without an official vendor fix).
Microsoft then provided a fix for Abdelhamid's bypass with January 2022 Windows Updates (assigning the "new" vulnerability CVE-2022-21919), but Abdelhamid took a closer look and found another way around it (the linked article is not available at the time of this writing).
We could easily reproduce this second bypass on fully updated Windows computers, except on Windows Server 2016. While our own micropatch was not bypassable using Abdelhamid's new trick, Microsoft modified the DLL we wrote the micropatch for (profext.dll), which meant we had to port our patch to the new version of this DLL to protect users who diligently apply Windows updates.
In short, CVE-2021-34484 is again a 0day on supported Windows versions. Somewhat ironically, affected Windows computers whose official support had already ended (Windows 10 v1803, v1809, and v2004) and have 0patch, did not have this vulnerability reopened.
- Windows 10 v21H2 (32 & 64 bit) updated with March 2022 Updates
- Windows 10 v21H1 (32 & 64 bit) updated with March 2022 Updates
- Windows 10 v20H2 (32 & 64 bit) updated with March 2022 Updates
- Windows 10 v1909 (32 & 64 bit) updated with March 2022 Updates
- Windows Server 2019 64 bit updated with March 2022 Updates